What Is NAT and How It Keeps Private IPs Secure

- 13 November 2025
When your computer connects to the internet, it doesn’t communicate directly using its private IP address. This is because private IP addresses are not visible to devices outside the local area network (LAN).
That is why all internet communication uses a public IP address, as they are visible outside the LAN. During online communication, something referred to as Network Address Translation (NAT) acts as an intelligent intermediary.
It is the responsibility of NAT to convert internal IP addresses on a network into public IP addresses so that devices/services can communicate over the internet. The purpose is to hide private IPs from outside networks to keep them secure.
This blog post explains what NAT (Network Address Translation) is, how it works, its different types, and how it keeps private IPs secure.
What is Network Address Translation (NAT)?
Network Address Translation (NAT) is a process, or you can say a technique, that is used by routers or firewalls to mask private IP addresses. It modifies the IP address information inside packet headers when the data is being transferred between a private and public network.
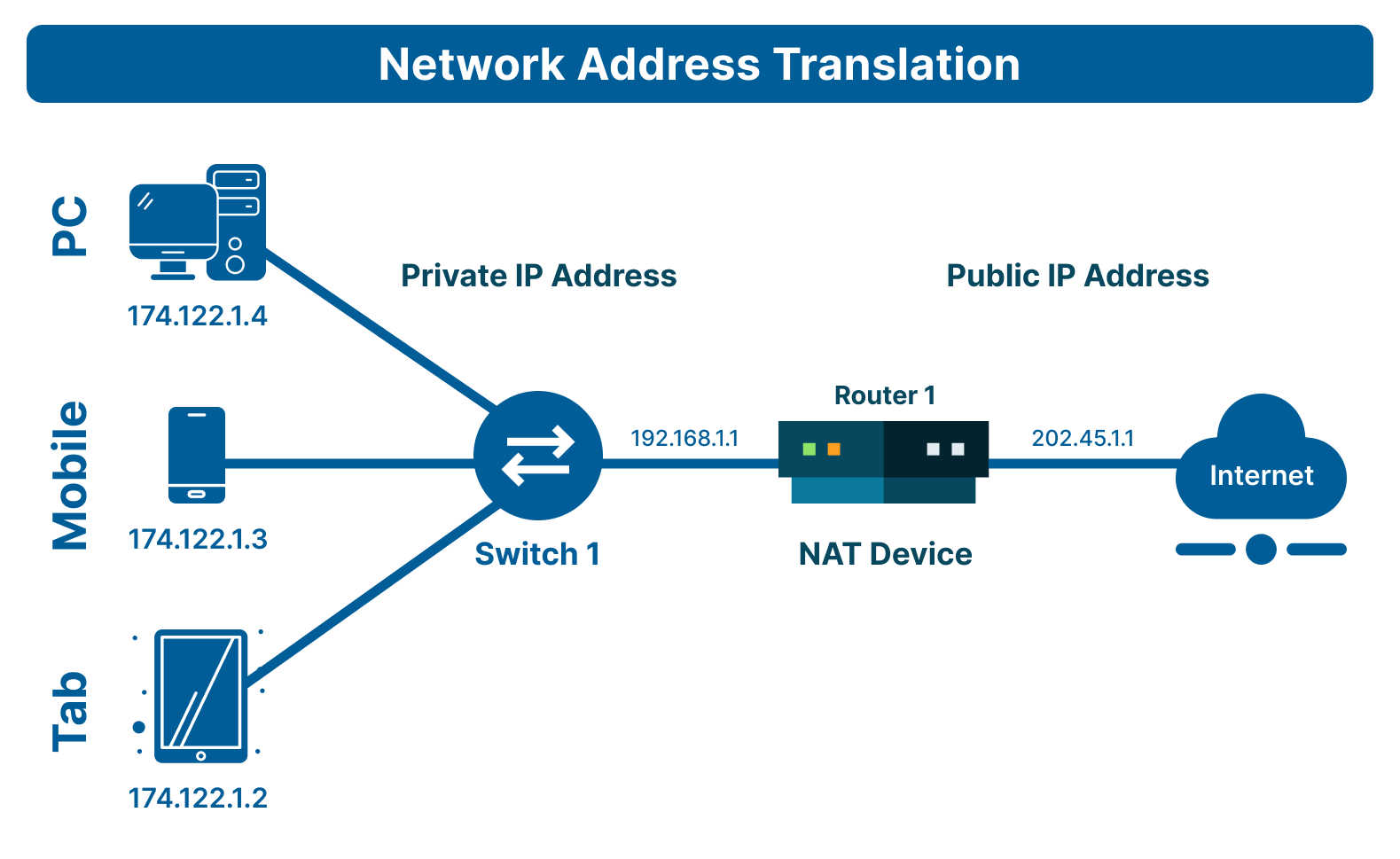
NAT allows multiple devices (e.g., computers, smartphones, smart TVs) within a LAN to share a single public IP address. In simple terms, all these devices from a single local network communicate over the internet using the same public IP address.
This IP translation process by NAT works both ways:
- Outbound Traffic: NAT changes a device’s private IP to the router’s public IP before sending data to the internet.
- Inbound Traffic: NAT reverses this process. It routes the response from the internet back to the correct device inside the private network.
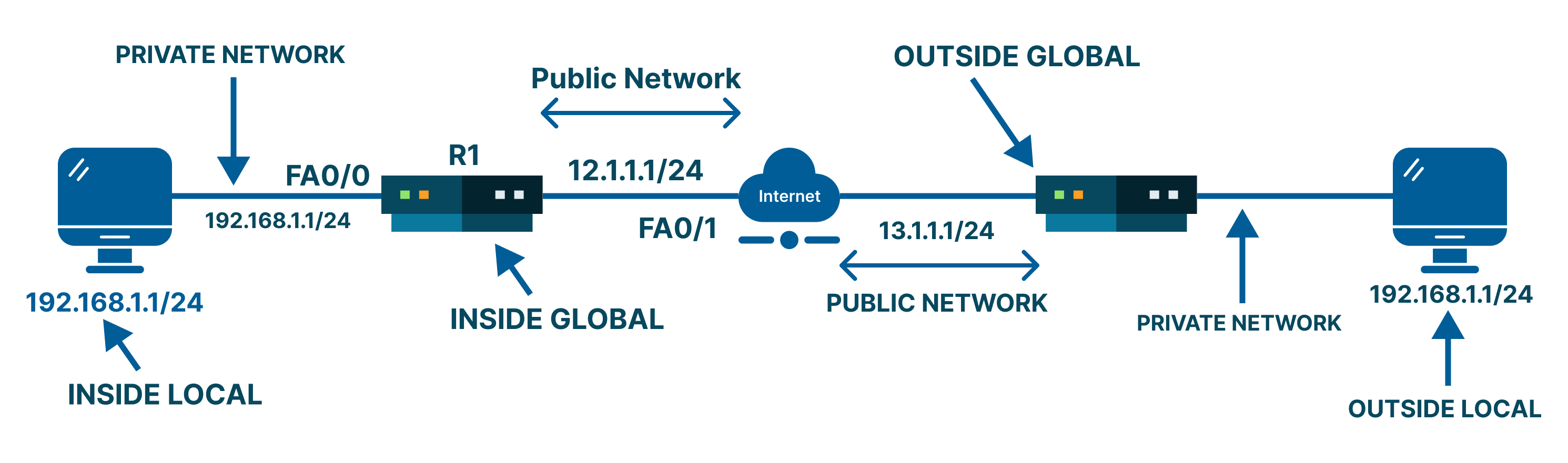
So, NAT acts as a middle-layer interpreter between your internal network and the external internet. The purpose of all this is to ensure smooth communication without exposing your devices directly.
You might be wondering why private IP addresses are hidden behind the NAT. Well, first, you should know the difference between a public and a private IP address.
For your convenience, we have written a blog post on the topic of Public Vs Private IP Addresses. Do check it now to avoid any confusion later.
Why Was NAT Created?
To understand why NAT was created, you must know the difference between IPv4 and IPv6 addresses.
IPv4 addresses are composed of 32-bit decimal numbers with four segments. Dots separate each of the four segments. The number range for these addresses is from 0 to 255.
Unlike IPv4 addresses, IPv6 addresses are composed of 128-bit numbers, separated into eight segments (also called hextets) of four hexadecimal digits. These segments are separated by colons rather than dots.
But why are we telling you this, since the discussion was about NAT creation?
Well, the thing is that in the early days of the internet, every device connected to the internet used a public IPv4 address. The problem is that IPv4 uses 32-bit addressing, as we just mentioned at the start of this section. This limits the total number of possible IPv4 addresses to around 4.3 billion.
The number might seem huge to you, but the reality is that the number of IoT devices on the planet is far beyond this. So, to sum it up, IPv4 addresses are insufficient as the world is exploding digitally.
Yet IPv6 addresses now reduce the dependency on NAT. However, before them, NAT was the only solution to address the IP address limit problem. Otherwise, the internet might fail to function and grow as it has today. But this doesn’t mean NAT isn't used at all now. ISPs and some enterprise or hybrid setups still use it.
How Does NAT Resolve the IP Address Limit Issue?
NAT solved the IP address crisis elegantly by introducing address reuse. Instead of assigning every device its own public IP address, NAT allows LANs to use reserved IP ranges (e.g., 192.168.x.x, 10.x.x.x, 172.16.x.x) internally.
And while the devices on the internal network use reserved IPs for internal communication, all of them share a single public IP for outbound traffic (i.e., communication over the internet).
To see this concept in action, you can check your public IP address online. You will find the address your router uses to communicate with the internet, not your device’s private IP address.
This process meant that:
- Thousands of devices could communicate with the internet using a single external identity.
- ISPs and organizations could conserve IPv4 addresses.
- The overall structure of the Internet remained stable and scalable.
Essentially, NAT extended the lifespan of IPv4 by multiplying the effectiveness of every public address.
How Actually NAT Works?
At its core, Network Address Translation (NAT) acts as a mediator between your private network (LAN) and the public internet (WAN). NAT basically operates via a router. It sits at the network’s edge, connecting your internal local network to your Internet Service Provider (ISP).
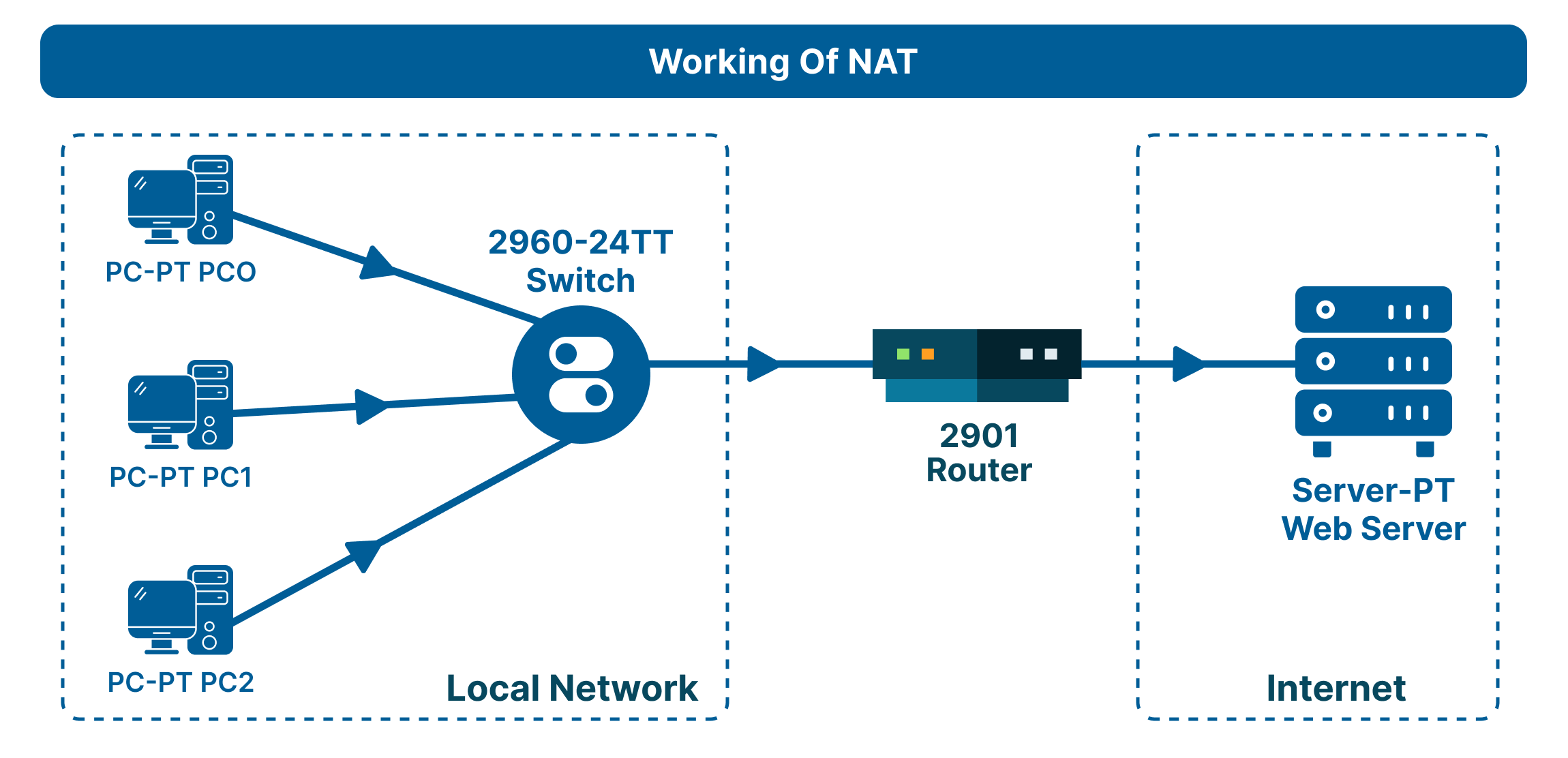
Here is how NAT works step by step.
- A device (e.g., your laptop) sends a data packet to an external server.
- The router intercepts the packet and replaces the private source IP with its public IP.
- The router records this mapping (private IP → public IP + port number) in its NAT translation table.
- When the external server responds, the router checks the table and sends the data back to the correct private device.
This translation occurs millions of times per second. All while creating a smooth, transparent experience for connected devices.
NAT Translation Table
The NAT table is the router’s memory of active connections. It tracks which internal device initiated which external connection.
Each entry includes:
- Private IP and port
- Public IP and port (assigned temporarily)
- Destination IP and port (the remote server)
When data returns, NAT matches the external port back to the correct private IP. Remember, the purpose is to ensure precise routing.
All the aforementioned mapping is time-sensitive. When a session ends or a session time period expires, the entry is deleted. This helps in maintaining both efficiency and security.
Common Types of NAT
Network address translation has three common types:
- Static NAT (One-to-One)
- Dynamic NAT (Many-to-Many)
- PAT or NAT Overload (Many-to-One)
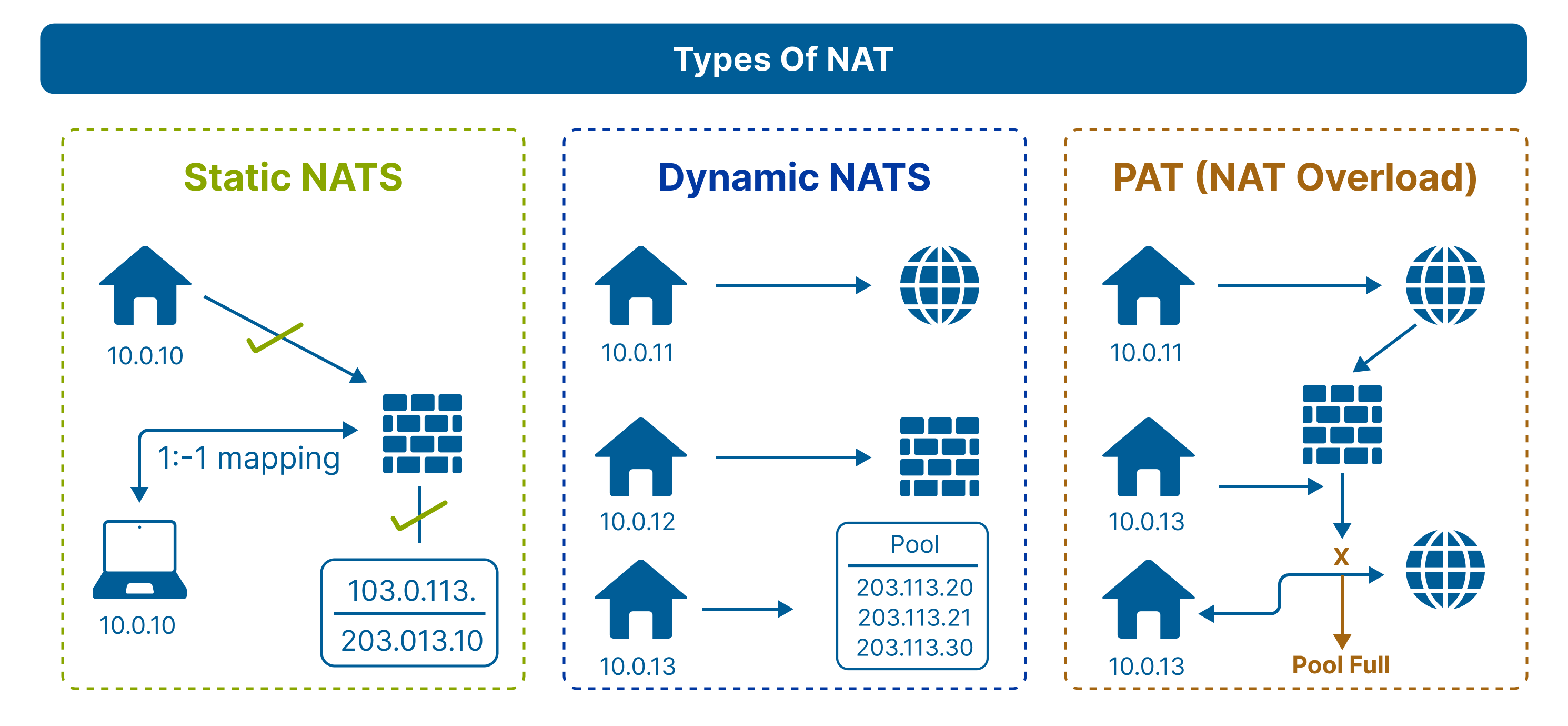
Below, the functionality of each is explained individually.
-
Static NAT
In this type of NAT, a single private IP is mapped (i.e., translated) to a single public IP address. Static NAT is usually used in web hosting and other applications where consistency with limited scalability is needed.
-
Dynamic NAT
In dynamic NAT, multiple private IPs are mapped to a pool of public IP addresses. However, this type of NAT is used only when the number of internet users on a network at a given time is predefined.
-
Port Address Translation (PAT)
This is the most commonly used type of network address translation and is also known as NAT Overload. In PAT, multiple private IP addresses from a single local network are mapped to a single public IP address.
All the devices on the LAN communicate outside over the internet using this single IP address. PAT distinguishes multiple internal connections by assigning unique source port numbers to each session. They help to divert incoming traffic to the relevant destination device.
How NAT Enhances Network Security?
As described at the beginning, NAT was designed to solve the problem of limited IP addresses. However, it also has a side effect, a positive one. That side effect is enhancing network security unintentionally.
When external devices on the internet look at your network, they see only your router's public IP address. NAT keeps your private IP address masked, which is how it protects it from external access.
In short, NAT only adds a layer of obscurity incidentally. Many beginners misunderstand NAT as a security mechanism, which it is not. So, do not mistake NAT for a firewall or an encryption layer; they are separate things.
This means that your internal systems remain invisible and unreachable unless you explicitly configure them to accept incoming connections.
In cybersecurity terms, this is known as network-level obfuscation. It significantly lowers the risk of:
- Port scanning attacks
- Direct intrusions
- Data exposure
Below, we explain how network address translation enhances network security in practice.
-
IP Concealment and Anonymity
NAT acts as an identity shield for internal devices on a local network. Each private device communicates using the router’s public IP. Doing this makes it almost impossible for an external attacker to determine:
- How many devices exist inside your network?
- What operating systems or open ports do they have?
- Which device initiated a connection?
This is one of the simplest yet most effective ways to minimize attack surfaces on a local network.
-
Filtering Unsolicited Traffic
Another security advantage of network address translation is its default-deny behavior. NAT only allows inbound traffic that matches an existing session in its translation table. Any random or unsolicited traffic from the internet is automatically dropped.
This behavior:
- Prevents DDoS and brute-force attacks from reaching devices directly.
- Acts as a built-in packet filter before data even reaches a firewall.
Know that NAT doesn’t analyze packet contents like a firewall does. However, its connection tracking logic blocks external access by default.
-
Limiting Lateral Movement and Internal Risks
Even if an attacker somehow compromises one device on a NAT-protected network, the structure of NAT helps contain the threat. This is because internal devices use non-routable private IPs, which prevent direct communication with external systems. Attackers cannot easily use internal routing to pivot or move laterally within the network, thanks to the NAT.
Bottom Line
Network Address Translation (NAT) was basically designed to overcome the shortage of IPv4 addresses. They mask the private IP addresses of internal devices on a local area network (LAN).
While masking the private IPs, they let all devices on a network communicate over the internet using a single shared public IP address. This resolves both the IP address shortage issue and also keeps your private IP address secure. Also, when the private IPs of a network are hidden, the chances of certain cyberattacks are automatically reduced.
We hope this blog post has helped you understand what NAT is, how it works, and how it keeps your private IP address secure. For network-related topics, do check out our blog section.
Related Blogs

Troubleshooting DNS Propagation - How to Fix Common Domain Connection Errors
Learn how to solve DNS delays and fix domain connection issues easily.
- 30 Jun 2025

What Is MAC Address Randomization and How It Keeps You Private
Understand how MAC address randomization works and how it helps keep your device activity private on public and unknown networks.
- 25 Jun 2025

What is a DNS MX Record?
Learn what MX records are and how they keep your emails flowing to the right inbox
- 24 Apr 2025